Monday, March 16, 2009
Saturday, March 14, 2009
Disable or Hide Administrative Shares
Hidden Shares:
A hidden share is identified by a dollar sign ($) at the end of the share name. Hidden shares are not listed when you look through the shares on a computer or use the net view command. Windows create hidden administrative shares that administrators, programs, and services can use to manage the computer environment on the network. By default, Windows can enable the following hidden administrative shares:
(1) C$ D$ E$ - Root of each partition. For a Windows workstation computer only members of the Administrators or Backup Operators group can connect to these shared folders. For a Windows NT Server/W2K Server computer, members of the Server Operators group can also connect to these shared folders.
(2) ADMIN$ - %SYSTEMROOT% This share is used by the system during any remote administration of a computer. The path of this resource is always the path to the system root (C:\Windows).
(3) FAX$ - On W2K Server, this used by fax clients in the process of sending a fax. The shared folder temporarily caches files and accesses cover pages stored on the server.
(4) IPC$ - Temporary connections between servers using named pipes essential for communication between programs. It is used during remote administration of a computer and when viewing a computer's shared resources. This share can be very dangerous and can be used to extract large amounts of information about your network, even by an anonymous account.
(5) NetLogon - This share is used by the Net Logon service of a computer while processing domain logon requests, and by Pre-W2K computers when running logon scripts.
(6) PRINT$ - %SYSTEMROOT%\SYSTEM32\SPOOL\DRIVERS Used during remote administration of printers. This shares may not be used , if you are not connect to any LAN /WAN. These shares are hidden, but available with full control to domain administrators. The drive letter, followed by the $ sign is the name, and it is shared from the root. When trying to attain a highly secure network, you may wish to address this potential security issue by disabling these shares, or at least restricting their permissions to specific users or services. Better practice to disable these hidden shares.
How to disable:
There are two ways to disable it.
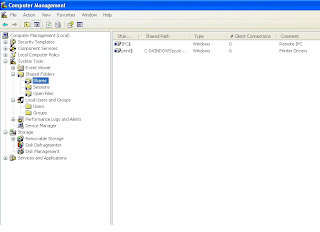
(1) Right Click My Computer -> Manage ->Shared Folders ->Shares -> Right Click on the Share and Disable.
(NOTE: If you disable an administrative share , it will not be automatically enabled after you restart your computer. )
(2) Permanently disable by using folowing regedit:
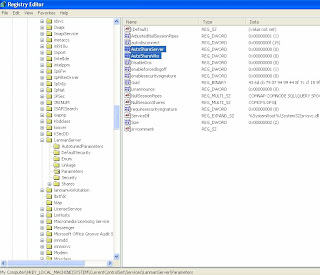
Hive:HKEY_LOCAL_MACHINE
Key:SYSTEM\CurrentControlSet\Services\LanManServer\Parameters
Name:AutoShareServer (for Windows 2000/2003/2008)
Name: AutoShareWks (for Win XP/Vista)
Type: REG_DWORD
Value: 0
Security Risk:
Unfortunately this registry hack does NOT stop the IPC$ share and this is a share that is often used by hackers to enumerate systems before attack since it can yield a wealth of information about your system names, your user names, and more. If your ACL permissions are not correct or you haven't disabled anonymous user access or you haven't disabled the guest account then this port can lead to total system compromise !
A hidden share is identified by a dollar sign ($) at the end of the share name. Hidden shares are not listed when you look through the shares on a computer or use the net view command. Windows create hidden administrative shares that administrators, programs, and services can use to manage the computer environment on the network. By default, Windows can enable the following hidden administrative shares:
(1) C$ D$ E$ - Root of each partition. For a Windows workstation computer only members of the Administrators or Backup Operators group can connect to these shared folders. For a Windows NT Server/W2K Server computer, members of the Server Operators group can also connect to these shared folders.
(2) ADMIN$ - %SYSTEMROOT% This share is used by the system during any remote administration of a computer. The path of this resource is always the path to the system root (C:\Windows).
(3) FAX$ - On W2K Server, this used by fax clients in the process of sending a fax. The shared folder temporarily caches files and accesses cover pages stored on the server.
(4) IPC$ - Temporary connections between servers using named pipes essential for communication between programs. It is used during remote administration of a computer and when viewing a computer's shared resources. This share can be very dangerous and can be used to extract large amounts of information about your network, even by an anonymous account.
(5) NetLogon - This share is used by the Net Logon service of a computer while processing domain logon requests, and by Pre-W2K computers when running logon scripts.
(6) PRINT$ - %SYSTEMROOT%\SYSTEM32\SPOOL\DRIVERS Used during remote administration of printers. This shares may not be used , if you are not connect to any LAN /WAN. These shares are hidden, but available with full control to domain administrators. The drive letter, followed by the $ sign is the name, and it is shared from the root. When trying to attain a highly secure network, you may wish to address this potential security issue by disabling these shares, or at least restricting their permissions to specific users or services. Better practice to disable these hidden shares.
How to disable:
There are two ways to disable it.
(1) Right Click My Computer -> Manage ->Shared Folders ->Shares -> Right Click on the Share and Disable.
(NOTE: If you disable an administrative share , it will not be automatically enabled after you restart your computer. )

(2) Permanently disable by using folowing regedit:
Hive:HKEY_LOCAL_MACHINE
Key:SYSTEM\CurrentControlSet\Services\LanManServer\Parameters
Name:AutoShareServer (for Windows 2000/2003/2008)
Name: AutoShareWks (for Win XP/Vista)
Type: REG_DWORD
Value: 0

Security Risk:
Unfortunately this registry hack does NOT stop the IPC$ share and this is a share that is often used by hackers to enumerate systems before attack since it can yield a wealth of information about your system names, your user names, and more. If your ACL permissions are not correct or you haven't disabled anonymous user access or you haven't disabled the guest account then this port can lead to total system compromise !
Friday, March 13, 2009
Hide Your Computer Name And Disable File Shares
NetBIOS Vs DNS:
Earlier Netbios was used instead of DNS for name resolution. But after 2000, Windows started using DNS (Domain Name System) and SMB (Server Messsage Block) Direct Hosting at TCP/IP port 445 for requests instead of port 139
.
The Risk:
.
The Risk:
This is basically used for name resolution and File sharing. NetBIOS on the WAN or over the Internet, however, is an enormous security risk. All sorts of information, such as your domain, workgroup and system names, as well as account information is obtainable via NetBIOS.
The SMB (Server Message Block) protocol is used among other things for file sharing in Windows OS. In Windows Servers it ran on top of NetBT (NetBIOS over TCP/IP), which used the famous ports 137, 138 (UDP) and 139 (TCP). In Windows, Microsoft added the possibility to run SMB directly over TCP/IP, without the extra layer of NetBT. For this they use TCP port 445. By standard both port 139 and 445 is open to get the highest degree of compatibility. A client will try to request on both ports and continue the communication on the port which responds first.
How to Disable?
Disable SMB use of Netbios port 139 (Forces use of port 445):
- On the Start menu, point to Settings, and then click Network and Dial-up Connections
- Right-click Internet facing connection, and then click Properties.
- Select Internet Protocol TCP/IP and select Properties
- Click Advanced and select the WINS tab
- Tick Disable NetBIOS over TCP/IP and click Ok
[HKEY_LOCAL_MACHINE \SYSTEM \CurrentControlSet \Services \NetBT \Parameters]Disable SMB use of port 139 and 445 (Disables nbt.sys driver):
SMBDeviceEnabled = 0
- Right-click My Computer on the desktop, and then click Manage.
- Expand System Tools, and then select Device Manager.
- Right-click Device Manager, point to View, and then click Show hidden devices.
- Expand Non-Plug and Play Drivers.
- Right-click NetBios over Tcpip, and then click Disable.
- On the Start menu, point to Settings, and then click Network and Dial-up Connections
- Right-click Internet facing connection, and then click Properties.
- Select Client for Microsoft Networks, and then click Uninstall.
- Follow the uninstall steps.
- Select File and Printer Sharing for Microsoft Networks, and then click Uninstall.
- Follow the uninstall steps.
If you are using a router as your Internet gateway then you will want to ensure that it does not allow inbound or outbound traffic via TCP ports 135-139.
If you’re using a Firewall then you should also block the same ports - TCP ports 135-139.
Thursday, March 12, 2009
Clipboard Hack:
Shocking News about CTRL + C :
Ctrl + C may be the most important and frequent work we do everyday. But it’s not very safe thing to do. Read on to know why? What happens when you press Ctrl + C while you are online?
We do copy various data by Ctrl + C for pasting elsewhere. This data is stored in clipboard and accessible from the net by anyone by using JavaScript and ASP. This is called clipboard Hack.
Just Try this:
1. Copy any text by Ctrl + C
2. Click on the link : http://www.sourcecodesworld.com/special/clipboard.asp
3. You will see the text you copied will be accessed by this web site.
Surprise!
Don’t you? It is extremely easy to extract the data stored in your clipboard to steal your sensitive information. So do not keep sensitive data (like Password, Credit card No, Pin No etc.) in the clipboard while you are connecting to net.
It’s true that the data last copied for paste operation can be stolen when you visit such web site which uses these scripting languages and your sensitive data will be saved on the database of others server.
How it works :
It can be done by using this simple JavaScript:
/*
var content = clipboardData.Getdata(“Text”);
alert (content) ;
*/
How to Overcome this hack :
To avoid this hack use following settings in your browser (IE):
1. Tools ->Internet options ->security ->Internet ->custom level
2. Scripting -> Allows paste operation via script ->disable.
Now the content of your clipboard is safe.
In latest versions of IE, this issue has been fixed :)
Ctrl + C may be the most important and frequent work we do everyday. But it’s not very safe thing to do. Read on to know why? What happens when you press Ctrl + C while you are online?
We do copy various data by Ctrl + C for pasting elsewhere. This data is stored in clipboard and accessible from the net by anyone by using JavaScript and ASP. This is called clipboard Hack.
Just Try this:
1. Copy any text by Ctrl + C
2. Click on the link : http://www.sourcecodesworld.com/special/clipboard.asp
3. You will see the text you copied will be accessed by this web site.
Surprise!
Don’t you? It is extremely easy to extract the data stored in your clipboard to steal your sensitive information. So do not keep sensitive data (like Password, Credit card No, Pin No etc.) in the clipboard while you are connecting to net.
It’s true that the data last copied for paste operation can be stolen when you visit such web site which uses these scripting languages and your sensitive data will be saved on the database of others server.
How it works :
It can be done by using this simple JavaScript:
/*
var content = clipboardData.Getdata(“Text”);
alert (content) ;
*/
How to Overcome this hack :
To avoid this hack use following settings in your browser (IE):
1. Tools ->Internet options ->security ->Internet ->custom level
2. Scripting -> Allows paste operation via script ->disable.
Now the content of your clipboard is safe.
In latest versions of IE, this issue has been fixed :)
Subscribe to:
Posts (Atom)
